
views
- True internet anonymity is nearly impossible. However, it is possible to take steps to protect your privacy and make it much harder to be tracked.
- Use an anonymous browser, like TOR as well as encrypted email and messaging services.
- Check the privacy settings for the apps, websites, and social media platforms you use.
Using Anonymity Tools and Practices

Use encrypted messaging services. If you want to send text or voice messages to other users, it's best to make sure you are using a messaging service that offers end-to-end encryption. [Signal] is one of the most secure apps for sending and receiving private messages. WhatsApp also uses end-to-end encryption, but it's not as trustworthy, and it's owned by Meta (the company that owns Facebook).

Use a VPN. A VPN (Virtual Private Network) encrypts everything you do on the internet, keeping you essentially anonymous on the internet. The general rule is that if you're using a solid VPN service, all of your internet activity will remain private. Using a VPN also prevents your ISP from seeing what you're doing online. However, many VPN servers do keep logs of your activities and can be subpoenaed in the event you're suspected of a crime. Although your ISP or other people on your local network can't see what you're doing when you're connected to a VPN, the VPN provider can. Unfortunately, there's no sure way to verify that a VPN provider doesn't log what you do on their service. Research VPNs thoroughly before selecting one.

Browse from a public Wi-Fi access point (with exceptions). To stay truly anonymous, your connection to the internet should not involve your ISP. That's where public Wi-Fi services come in. However, it's super important that you not pass any personal information over one of these networks that you don't want others to see. Do not connect to a public access point if you need to do something private pertaining to your own identity, such as banking or dealing with social security numbers. Even if you see that there's an open network available, make sure you know it's the legitimate one for the location. Hackers often set up Wi-Fi networks that look similar to existing ones specifically to steal data. Even if the wireless network is legit, someone shady may be running a tool that can sniff all active traffic. A good quadruple-whammy solution would be to spoof your IP address, connect to public Wi-Fi, connect to a VPN, and then browse through TOR.
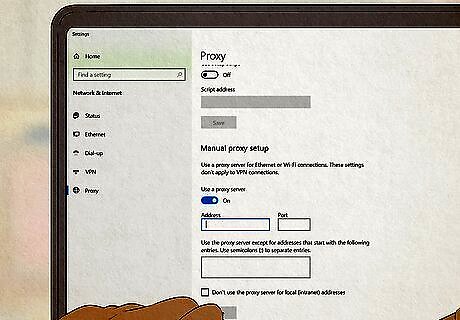
Use a proxy server. A proxy server works much the same way as a VPN. They mask your IP address and make it harder to be tracked. Proxy servers tend to be less secure than a VPN, but they tend to be cheaper (often free). Proxy servers are great to connect to when you are using a public Wi-Fi network.
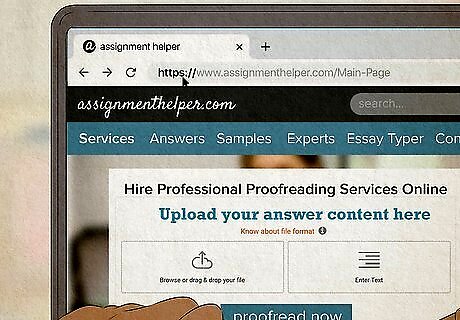
Check that a website is secure. If you need to pass personal information, such as your name, bank account, credit card, or social security number online, make sure the website is secure. Check the address bar in your browser and make sure the URL starts with "HTTPS" instead of "HTTP."
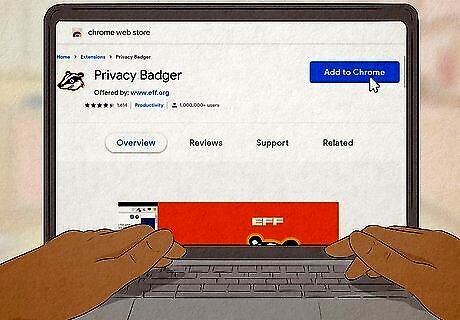
Install privacy-protecting browser add-ons/extensions. If you want to avoid being tracked on the web, there are a variety of tools you can install through your web browser: Privacy Badger: This tool, designed by the Electronic Frontier Foundation (EFF) blocks third-party tracking cookies so advertising services and websites can't keep tracking you once you leave their pages. You can get Privacy Badger for Firefox, Edge, and Opera web browsers. Ghostery: This is another tool similar to Privacy Badger that blocks third-party tracking cookies. It also blocks ads and allows you to customize your blocking preferences. Available for Firefox, Chrome, Edge, and Opera. NoScript: A Firefox-only add-on that blocks all JavaScript on websites. Since many websites need JavaScript to work properly, you can manually manage a whitelist to allow JavaScript on sites you trust.

Use an anonymous web browser. The Tor web browser routes all of your traffic through its own network, making your web browsing virtually anonymous. When you browse through Tor, it's very difficult (not impossible, but close) for your ISP, a network administrator, or a Wi-Fi hacker to see the websites you visit or the sites you sign in to. Another anonymous browser you can try is Brave. Never download Tor from anywhere other than https://www.torproject.org. If you don't want your ISP to know that you browse with Tor, you'll need to use it over a VPN.
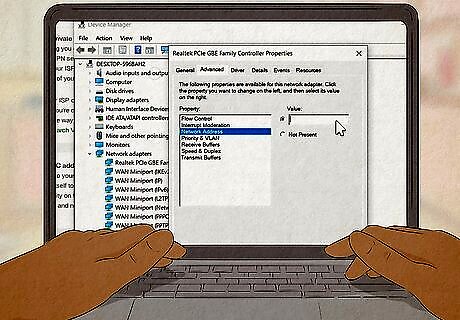
Spoof your MAC address. Your MAC address is the hardware address that identifies your computer to your router. Every time you connect to a network, your MAC address broadcasts itself to announce your presence. You can use a fake MAC address to anonymize your activity on the network. However, websites you visit and sign into will still be visible to your ISP and network administrators, although you can use a VPN as another layer of protection.
Use a password manager. Many web browsers have the ability to store your passwords for your. While this is convenient, it's not very secure and leaves you vulnerable to hackers. Use a password manager instead. This allows you to create a strong and unique password for every website you visit and stores your passwords securely.
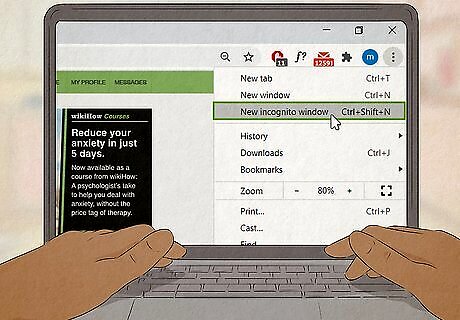
Try your browser's private mode. If you're worried about people finding out what you do on a shared computer, browse in your web browser's private or incognito mode. Nearly all web browsers come with a built-in browsing mode that prevents your web browsing history and cache from saving to your computer. Chrome allows you to open a new "Incognito" window, Safari and Firefox allow you to open "Private" windows, and Edge calls their private mode "In Private."
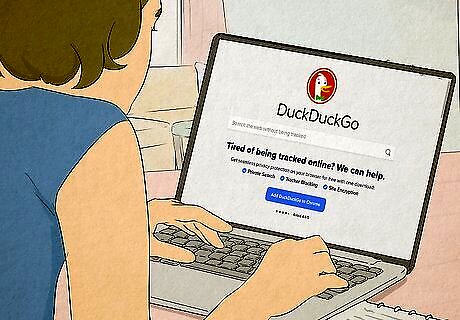
Use an alternative search engine that focuses on privacy. Search engines like Google, Bing, and Yandex store your search queries along with your IP address (and account if you are logged in). They also use cookies to track how you use the search engine and to keep tabs on what sites you visit. This information is compiled and analyzed to more accurately target ads and provide relevant search results. To avoid this sort of tracking, use an alternative, privacy-focused search engine like DuckDuckGo or StartPage.

Use an encrypted email service or a throwaway email address.Use an email service that provides end-to-end encryption, such as ProtonMail, Tutanota, etc. Services like Guerilla Mail allow you to create a temporary disposable email. Make sure the email you create does not contain any personal information and is not tied to any accounts that store your personal information. Some popular free email providers that make it fast to sign up for new accounts are Gmail and Yahoo Mail. Try Protonmail if you want to send encrypted email messages without providing any personal data.

Use zero-knowledge encrypted cloud storage. Cloud storage services, like Google Drive, and Dropbox can view and monitor all files you upload. If you need to use cloud storage, use a zero-knowledge service with end-to-end encryption. These services claim to not know what the users upload to their servers. They also feature client-side end-to-end encryption to prevent those who don't have the encryption key from viewing your files. Zero-knowledge cloud storage services include Sync.com, SpiderOak, IceDrive, and MEGA. The safest way to store your files is on an encrypted external hard drive or flash drive.
Learning How You're Tracked Online

Be aware of what your ISP can track. Your Internet Service Provider (ISP) is the service you use to connect to the internet. When your modem or router makes a connection to the internet, it is assigned an IP address—this address is trackable to your account. This means that at the very least, anyone who can see your IP address can identify your ISP. If you do something illegal from this IP address, a government jurisdiction (such as the local police or even the FBI) can serve a subpoena to your ISP to find out who was using that IP address at that time, and what sites and services were accessed. Some other things that your ISP can identify based on your IP address: Website content: If you visit https:///www.wikiHow.com while connected to the internet, your ISP logs that domain name. In theory, they can tell how often you visit wikiHow, what you downloaded (if anything), and how long you spend on the website. Although they can find this information, they won't be watching unless they are serviced with a subpoena that requires them to do so. If you frequently visit websites that focus on illegal content, your activity may be flagged by your ISP. Your MAC address: A Media Access Control (MAC) address is an address assigned specifically to your computer's Wi-Fi or network card. Your ISP can determine which MAC address on your network was used with an IP address at a specific time—this means that if you're on your school, work, or home network, the network administrator can identify the sites and services used by your computer. Port numbers: If you make connections to (or receive connections on) certain port numbers, your ISP can often determine what kind of services you're using, such as browsing the web (usually ports 443 and 80) or sending emails (usually ports 25, 587, 587, or 465). Your VPN service: If you use a VPN on top of your internet connection to hide what you're doing online, your ISP can see which VPN you're using and when you connected. They cannot, however, see exactly what you're doing on the VPN.

Be careful what you post online. Social media is ubiquitous these days. Everyone has a Facebook, Twitter, Instagram, or TikTok, account, but be aware of what information these websites can reveal about you. Not only do they track your personal information and use it for targeted advertising, but the stuff that you post can reveal a lot about your personal life. Your social media profile often contains information such as your name, education, work, and where you live. All of this information can be used to track you. Be aware of what your post says about you in aggregate. An individual post may not seem all that sensitive, but all your posts taken together can reveal a lot about you. Information you share can paint a picture of your overall personality and temperament. Hackers and scammers can use this information to target you. Employers can use this information to decide if they want to hire you (or keep you employed). Avoid posting pictures of your children or family, or their names. Be aware of what's in the pictures and photos you post. They may contain information about you, such as your license plate number, or recognizable landmarks that point to the area you live in.
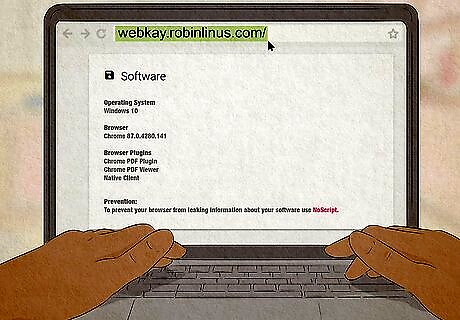
Find out what websites and phone applications can learn about you. Most websites make money by displaying ads. Many mobile applications (especially free apps) also collect information about you. To successfully get visitors to click (and make purchases from) ads, site owners and ad networks need to know what your interests are and how you use the internet so they can show you relevant ads. Websites and phone applications collect data by installing tracking cookies on your computer or mobile phone, which can tell them what other sites you visit, your location, the browser and operating system you're using, how long you spend on their site, which links you've clinked, whether you're signed in to certain social media sites like Facebook, what you search for, and even your laptop's battery level. All of this occurs automatically when visiting sites doing this data mining, without you noticing. To get an idea of what a website can learn about you just by visiting it once, check out https://webkay.robinlinus.com. As soon as you load the page, you'll see some startling information. Not all cookies are bad. In fact, it's important to allow some cookies. Cookies are used to store pieces of data on your computer to make your browsing experience easier. For example, cookies make it possible to sign in to accounts that require passwords, add items to shopping carts, and more. However, some cookies, called "tracking cookies" or "third-party cookies" are meant to track your activity on all websites, just not the one you're visiting. When installing a new app on your phone, be aware of what permissions it asks. Do not allow it access to any information it doesn't need. For example, if an app asks for access to your locations, ask why does it need this information. If you don't feel it needs this information, do not allow it access to your locations.

Know your wireless access point. Do you connect to public Wi-Fi access points, such as those in cafes? How about at your friends' homes? The reality is that any time you connect to public Wi-Fi (or a Wi-Fi access point that you don't manage yourself), there's a possibility someone is actively snooping your data. If a malicious user has access to the public Wi-Fi access point, connecting your computer, phone, tablet, or smartwatch to that wireless network can see almost everything you do while signed in—including entering your passwords, viewing your banking data, and finding out your contact info.


















Comments
0 comment