views
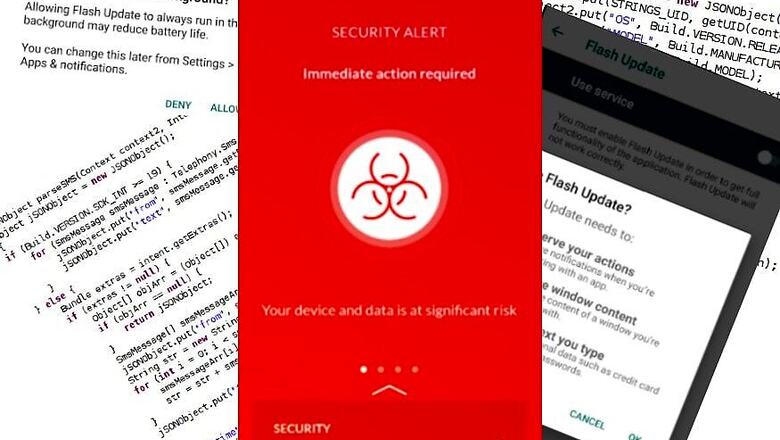
A new strain of malware, named EventBot, is being spread across the internet through unofficial app download websites with the key target of stealing your money. The malware is specifically targeted at Android devices at the moment, and according to cyber security research firm Cybereason, can be a particularly tricky trojan to deal with in the long run. EventBot is using third party app download sites and disguising itself as applications such as Microsoft Word, Adobe Flash and others.
Once downloaded, the application starts asking for numerous deep-level permissions on an Android device in order to run, which include controlling system alerts, reading external storage content, installing additional packages, access internet and read network state, ignore any battery stamina mode restrictions, wake device from lock, continue running and accessing data in the background, auto-initiate upon reboot, and send, open and read SMS messages.
If enabled by any unsuspecting user, EventBot can then access notifications about other installed apps, and read content of other apps. This further lets it gain access to Android's accessibility services in order to read lockscreen and in-app PINs. The background data and continuous operation is utilised in order to then send all the gathered data to a remote server controlled by attackers, all in an encrypted package. Its permission to snoop SMS messages further allows it to bypass any two-factor authentication setup by users, and also tap in to relatively secure cryptocurrency wallets that may be installed on phones.
The Cybereason post, written by cyber security researchers Daniel Frank, Lior Rochberger, Yaron Rimmer and Assaf Dahan, state that EventBot is a rare instance of an early stage malware being detected. The trojan is being iteratively updated, and hence stands the chance of developing into a critical malware that can wreak potential havoc around the world. The post states that EventBot is largely targeting financial apps based in USA and Europe at the moment, but include services such as HSBC, Paypal, Coinbase and more in the list of active EventBot targets, which makes it relevant to India as well.
The post further reads, "Though EventBot is not currently on the Google Play Store, we were able to find several icons EventBot is using to masquerade as a legitimate application. We believe that, when it is officially released, it will most likely be uploaded to rogue APK stores and other shady websites, while masquerading as real applications."
To stay safe, users should always ideally stick to downloading apps only from the Google Play Store. The official Android app store, although being under fire for monopolistic practices, does include a host of safeguards such as app policies that prevent a service from asking for too many deep-level permissions. It also offers Google Play Protect, which is an additional safeguard against such trojan files being part of real smartphone apps.

















Comments
0 comment