views
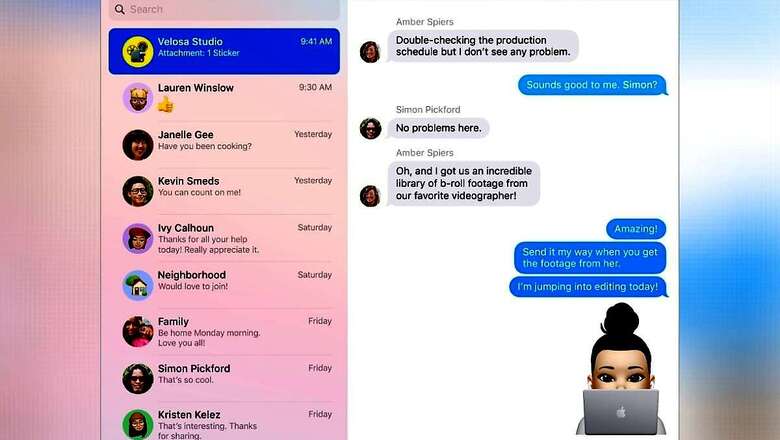
Apple has added a new security system on iPhone and iPad models, specifically designed to protect malicious attacks against the iMessage platform. The security sandbox tool BlasDoor was reportedly rolled out with the iOS 14 update in September and discovered after reverse-engineering the macOS 11.1 running on the M1-powered Mac Mini. It is said that the service is written in Swift, a common memory-safe language that makes it “significantly harder” to introduce classic memory corruption vulnerabilities into the code base – in this iMessage.
The development was discovered by Samuel Groß, a security researcher with Google’s Project Zero team. In a blog post, the researcher details that the BlastDoor service is a basic sandbox, that is a type of security service that executes code separately from the rest of the operating system. Notably, Apple has already deployed several sandbox mechanisms on iOS 14; however, BlastDoor is specifically tailored for the iMessage app. As explained by ZDNet, the BlastDoor takes incoming messages and processes their content inside a secure and isolated environment, where any malicious code hidden inside a message can’t interact or harm the underlying operating system t extra users’ data.
The in-the-wild zero-click iMessage exploit detected by @citizenlab last year apparently didn’t affect iOS 14. I did some reverse engineering to see what had changed in that release and found lots of cool things! https://t.co/5oCHIo4CpN— Samuel Groß (@5aelo) January 28, 2021
Over the last few years, Apple’s homegrown iMessage app has been criticised by security researchers of a poor job of sanitising incoming malicious messages. In December 2020, Canada-based Citizenlab published ‘The Great iPwn,’ detailing how journalists were targeted with an iMessage zero-day exploit allegedly by Israeli technology firm NSO Group. The iMessage vulnerability allowed hackers to execute arbitrary commands remotely to gain access to the smartphone. Apple with its new BlastDoor service will hope to strengthen the security around the iMessage app.
Notably, security researcher Groß along with his Natalie Silvanovich found ‘zero interaction’ flaws in iMessage in 2019 that could allow attackers to read the content of files being stored on an iPhone, without requiring users to interact with any notification or message.
Read all the Latest News, Breaking News and Coronavirus News here

















Comments
0 comment